Authy is a security application built on a foundation of encrypted, multi device synchronization, designed to provide both robust protection and practical convenience.
Authy app holds a 3.8 star rating from over 800,000 user reviews on the Google Play Store. With a download size of about 50MB, it is designed for a broad age range, from tech savvy individuals managing cryptocurrency exchanges to any professional securing their work email and cloud storage.
How Authy Generates and Manages Access
Authy works relies on Time based One Time Passcodes (TOTP). These are the standard six or eight digit codes that refresh every 30 seconds, generated directly on your device. You enter this code after your password to complete a login.
The critical differentiator for Authy two factor authentication is what happens behind the scenes. Unlike simpler apps, Authy encrypts your secret keys and securely backs them up to the cloud. This process is the cornerstone of the Authy multi device sync feature. It means your tokens are not trapped on a single piece of hardware. You can access them from your phone, tablet, and desktop simultaneously, and, most importantly, recover them if your primary device is lost, damaged, or replaced.
This system maintains utility even without a network connection. The Authy offline token generation ensures you can still access your codes on a device that has been previously synced, providing security in areas with poor or no connectivity.
The Defining Features of the Authy Experience
What truly separates Authy are the pillars of its design. The Authy multi device synchronization is a game changer for convenience. Adding an account on your phone automatically makes it available on your authorized desktop app, eliminating the tedious process of rescanning QR codes on every device.
This is all protected by encrypted cloud backups on Authy. This is not just a sync feature; it is your recovery plan. It directly solves the primary fear associated with 2FA: permanent lockout. Furthermore, its cross platform availability for Authy means this protection extends across Android, iOS, Windows, macOS, and as a Chrome extension, creating a consistent security layer over your entire digital ecosystem.
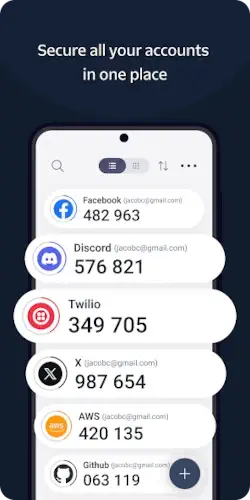
The app supports a vast array of services, from mainstream platforms like Facebook and Dropbox to financial and crypto exchanges supported by Authy, making it a versatile tool for securing a diverse portfolio of online accounts.
Navigating the Authy Application Interface
The application interface adheres to a philosophy of functional clarity. The main screen is a straightforward, list based layout that displays your added accounts alongside their current codes and countdown timers. The design prioritizes quick readability, ensuring you can find the right code without distraction or delay.
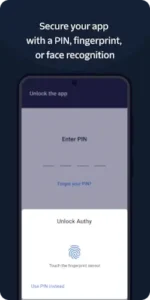
The Authy setup guide process is intuitive. Adding a new account typically involves scanning a QR code from the service you want to protect. The app handles the configuration automatically. To protect this centralized hub of access, the application itself can be secured with a PIN or biometric lock, ensuring that even if your device is unattended, your tokens remain private.
For those evaluating options, a similar and highly regarded security application is Google Authenticator, which focuses on a simpler, offline only approach. However, for users who prioritize seamless recovery and access across all their devices, Authy’s synchronized model presents a compelling argument for consolidating your security.
Authy User Reviews
The consensus among users highlights clear strengths. The profound peace of mind provided by encrypted Authy backups is the most frequently praised feature. Knowing your tokens survive a phone upgrade or a misplaced device transforms a potential security crisis into a simple login. The utility of multi device sync in Authy is a close second, allowing you to approve a sign-in on your laptop or retrieve a code from your tablet without needing your phone nearby. Its reliable offline access ensures security is not dependent on a perfect cellular signal.
However, no system is without its considerations. The most critical point of friction is the absolute necessity of remembering your Authy backup password. Losing this password means the encrypted backups are permanently inaccessible; not even Authy support can recover it. Some power users with extensive account lists also express a desire for more advanced organizational tools, such as folders or custom sorting, to manage a long scroll of tokens more efficiently.
Authy Tips for Proactive Management
A smooth experience with the Authy app hinges on proper setup and a few key habits. The initial configuration is a logical guide, but your first action should be to enable encrypted backups. This is the non negotiable step that defines the Authy authenticator value proposition.
For ongoing management, several Authy tips are invaluable. First, use clear, descriptive labels for each account as you add them. “Work Slack” and “Coinbase Pro” are far more scannable than generic defaults. Second, ensure your device’s time is set to synchronize automatically; even a slight drift can cause your time based codes to fail. Finally, understand the process for adding new devices: you will need to authorize them from an already registered device, a security measure that prevents unauthorized access to your token vault.
Authy Similar Apps in the Security Landscape
Where does Authy fit among other authenticators? A neutral comparison helps clarify its niche. Google Authenticator is a minimalist option, generating codes offline without any cloud backup. Microsoft Authenticator offers backup and sync but is deeply integrated with the Microsoft ecosystem. Duo Mobile is often favored in corporate environments for its enterprise management features.
Authy similar apps often lack its specific combination of cross platform availability and user controlled, encrypted backups. Authy’s unique position is that of a cross platform, backup oriented solution for individuals who want to own their recovery process and access their tokens from any trusted device, without being tied to a specific tech ecosystem.
Conclusion :
The Authy authenticator serves as a highly accessible and convenient security tool that effectively solves the core problem of 2FA portability and recovery. It makes robust security manageable by ensuring your digital keys are not just secure, but also resilient and readily available.
For anyone who values redundancy and the practical ability to access their authentication tokens from any of their devices, Authy remains a top tier choice. It represents a pragmatic balance between strong security and the reality of our multi device digital lives.
Frequently Asked Questions
What is the primary benefit of using Authy over SMS for two factor authentication?
SMS messages can be intercepted through SIM swapping attacks. Authy generates codes directly on your device, making them immune to this threat. It also works without a cellular signal, providing security and access anywhere.
How do I complete an Authy download and set it up on multiple devices?
You can get the Authy app from the official Google Play Store. During the initial Authy download and setup, you will register a phone number and enable multi device sync in the settings. This allows you to install Authy on other devices and link them to your account.
Is the cloud backup feature secure, and what happens if I forget my backup password?
The backups are encrypted with a password you set, and even Twilio cannot access your data. This means if you forget your Authy backup password, the encrypted data is irrecoverable. You would need to reset your Authy account and re-add all your services. It is crucial to remember this password.
Can I use Authy for my work accounts and cryptocurrency exchanges?
Yes. The Authy app supports standard two factor authentication protocols used by thousands of services, including many enterprise platforms (like Slack, AWS) and major cryptocurrency exchanges (like Coinbase). Its broad compatibility is one of its key strengths.
Where can I find technical details or get support for the application?
For technical specifics on the protocols it uses, you can check the Wikipedia page for Authy. If you encounter issues with the application itself, you can contact Twilio support at support-authy[at]twilio.com.